bitcoin-qt wallet encryption
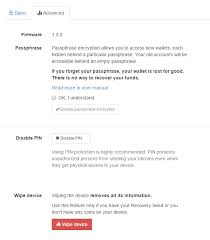
There are several advanced settings that can be configured after setting up your TREZOR device.For the most part, these settings can be accessed by pressing the Advanced settings button right after you have plugged your TREZOR.Disable PIN protection It is possible to disable PIN protection using the Disable PIN button, however, we do not recommend to do so, as PIN protection reduces the risk that a person with physical access to your TREZOR device will be able to steal your bitcoins.TREZOR Wallet will ask you for your PIN the first time you try to make a transaction after plugging in your TREZOR and it works in such a way that even the computer you use with your TREZOR never finds out your PIN.Warning We DO NOT recommend to DISABLE PIN PROTECTION even if you have configured a passphrase for your TREZOR!Using passphrase encrypted seeds In addition to a PIN, it is possible to add a passphrase to your TREZOR.This has the advantage of making your TREZOR impervious to physical attack.
Even if your TREZOR were to be stolen and the chip examined under an electron microscope to discover your recovery seed, your bitcoins would still be safe!A passphrase can be any word or any set of letters that you might use as a password.Your passphrase should be memorable, though.You typically would not write it down anywhere, to eliminate any possibility of it being discovered.One limitation of the passphrase approach is that you have to enter your passphrase into the computer that you use with your TREZOR.For this reason, you should not be tempted to disable your PIN even if you use a passphrase as well!The flip side to this extreme level of security is that if you forget your passphrase your bitcoins are lost.Note If you have stored some funds in your TREZOR before setting up the passphrase encryption, they will not appear after enabling the passphrase.But don’t worry, they are not lost.You can access them by entering a empty passphrase.HashNest • Comprehensive Discussion • CONNECT • Posted 2017-03-11 05:27:05 • Reply by vaveepula at 2017-06-24 02:06:33 • Read 725 times My name is Rob.

Product Manager of Connect.im.Today,I have the honour to introduce a new product that developed by our team.Named Connect.IM Connect is an open source point-to-point encrypted instant messaging APP.You can use CONNECT to send texts, voices, pictures, videos and even Bitcoin.In both one-on-one chat and group chat, all the messages including text, picture, voices, video, etc. are sent via the shared key encryption negotiated by both sides of the chat.Any third party other than the both sides including the server can't decrypt the messages.As known as bitcoin, if there is no private key, then no one can steal your bitcoins.Similarly, user’s ID of Connect are generated based on BTC algorithm, if there is no private key, then no one can not steal the messages of the chat.Connect uses advanced and open-source symmetric encryption algorithms to secure both parties' information and the communication between the client and the server, and anyone can authenticate.The end-to-end encrypted communication between both sides of the session as well as the encrypted communication between client-side and server uses the key negotiation method to make double layer encryption, with the steps as below: 1.
Session initiator_A use the agreed ECC (elliptic curve cryptography) locally to generate a pair of key(Public_key_A,Private_key_A) and a 512-bit random number salt, and send the random number “saltA” and “Public_key_A” to receiver_B after AES256-GCM encrypted 2 The receiver_B receives “PublicKey_A” and “saltA” after decrypt.
litecoin usd exchange ratethen use the same ECC (elliptic curve cryptography) generate a pair of key(Public_Key_B,Private_Key_b) and a 512-bit random number salt, and send the random number “saltB” and “Public_key_B” to initiator_A after AES256-GCM encrypted.
ethereum understanding3 Initiator_A get “saltB” and “Public_key_B”.
bitcoin cafe parisThen both initiator_A and receiver_B get ECDH_Key ECDH_Key = ECDH(PrivateKey_A, PublicKey_B) = ECDH(PrivateKey_B, PublicKey_A) 4 Then the PBKDF2key expansion algorithm to obtain the negotiated key "K" by ECDH_KEY and random number salts of both sides.
bitcoin geography
Shared_key = PBKDF2(HMAC-SHA512, ecdhKey, saltA^saltB, pow(2, n), 256) ,(n=12) 5 The key agreement is completed, and both sides of the AB erase their session key pairs from their respective memory.
bitcoin is approved by rbi(ECDH_Key,PublicKey_A,PublicKey_B) 6 Sessions following, both sides of the AB encrypt and decrypt messages using 256bit Shared_key and AES-256-GCM algorithm.
bitcoin escrow scriptThe negotiated key is updated when a new session is created each time.
bitcoin kaufen ohne bankThe encrypted communication channel established by the above process ensures that communication contents are not leaked under the condition that the network flow is completely monitored.
bitcoin coin asic
Even if the private key of server-side is mastered by the monitor, the monitor can't decrypt the actual communication contents () according to the private key of server and all network flows, and even can't know the person who is logged in or the side to whom the messages are sent.
female seeds bitcoinSo this solution has the nature of forward secrecy because the session key pair will be erased by both sides from their respective memories after completion of negotiation.Why do we need CONNECT?Different from other instant messaging tools provided by other Internet giants, Connect offers a higher level of security and privacy protection.It protects your chatting contents from being eavesdropped by any third party such as employers and government.It protects your personal data such as telephone numbers and friends from being utilized by any third party such as marketing personnel and advertisers.Considering "PRISM" scandal as well as multiple network fraud cases caused by information leakage, each of us should defending "freedom of speech" and "personal privacy”.

So Connect is suitable for everyone.Why Connect APP contain bitcoin wallet?First, user’s ID of Connect are generated based on BTC algorithm, and the user system is established based on decentralized BTC blockchain network.So, Connect APP itself can be used as Bitcoin Wallet.As a decentralized financial network which do not rely on any institution or government, Bitcoin is highly consistent with the product philosophy of "Connect".Connect doesn't wish users' data to be monitored by any institution.It is greatly convenient for BTC users to use the interactive mode based on social network and chat session to realize BTC transfers.You don’t have to remember the bitcoin address of your friends.Instead that transferring the bitcoins is as simple as sending a message.[size=16pt][b]It is onchain or offchain bitcoin wallet?Because the private key of user is stored in the device locally, and each BTC transaction should be made by the private key signature of the user, this is a onchain wallet.The server does not store the user's private key, ensuring that the user can fully control their own funds.

But in many cases, users are easy to lose their private key.We provide a compromise, users can bind their mobile phone, after verified, set a password for encrypted private key and backup on server, server does not store user’s password.Even if the phone is lost, user can use password decrypt and recovery the private key after new phone verified.If the user has doubts, can also choose “Generate a local account”, keeping private key by oneself com fully.[size=16pt][b]Transfer bitcoin as simple as sending a message[/b][/size] Transfer bitcoin as simple as sending a message.You don’t have to ask your friend’s bitcoin address in other way.Send bitcoin or payment request in the chat window just like sending a message.You can sent bitcoin link via other IM APP such as "Whatsapp" "Messabfer" "Wechat".your friend who got this link would got bitcoin ofter install Connect APP.Lucky packet is a kind of function sending BTC to your friends as a gift.Your friends won't know the BTC quantity they have obtained untill after opening the red envelope.