bitcoin com boleto

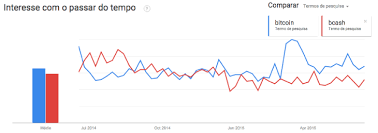
Gateway de Pagamento MultiCoin: Bitcoin, Litecoin e Dogecoin Aceite pagamentos Bitcoin, Litecoin, e Dogecoin hoje!Voltar Por que utilizar moeda virtual?O gráfico acima já resume bem a procura por termos relacionados a moedas virtuais, no caso Bitcoin tem despontado no Brasil.Proteção contra fraude: Qualquer negócio que aceita cartões de crédito, PayPal sabe bem o problema causado por pagamentos cancelados posteriormente.Fraudes de estorno resultam em restrição nas vendas e aumento dos preços e acaba penalizando os consumidores.Pagamentos com Bitcoin são irreversíveis e seguros, fazendo com que o custo do risco por fraude não caiam mais sobre os ombros dos comerciantes.Mas o que é e como funciona o Bitcoin, Litecoin ou Dogecoin?Bitcoin, Litecoin ou Dogecoin é uma moeda, assim como o real, o dólar americano, o peso e muitas outras.Seu funcionamento ocorre através de um banco de dados que registra as transações, além de, utilizar criptografias como forma de segurança, ou seja, certificar que bitcoins por exemplo só podem ser gastas pelo dono (por isso, moeda criptográfica).
Sendo que, podem ser enviadas pela internet para qualquer pessoa que tenha um endereço de bitcoin.Por não ter uma entidade administradora central, torná-se inviável que qualquer autoridade, governamental ou não, manipule o valor de bitcoins ou induza inflação.Como é realizada troca?Quando um usuário transfere bitcoins para outro usuário, o primeiro cede a propriedade dos bitcoins ao adicionar a chave pública do outro usuário nos seus bitcoins e assinando a transação com sua própria chave privada, comunicando essa transação na rede P2P, que valida a transação.Essa validação é registrada numa lista alimentada por todos os usuários conhecida como Block-Chain.Bitcoin e o E-Commerce Os varejistas tem aderido pouco a pouco as moedas virtuais principalmente ao bitcoin, aceitando a moeda para pagamento de produtos dentro das lojas virtuais.Segundo a matéria publicada na revista Exame, sites como o Tiger Direct e a Overstock já receberam mais de 1 milhão de dólares em 2014 em pagamento via moeda virtual.

Wallet/Exchange já integrados .br Ainda na dúvida?Y los ganadores del Bitcoin Trading Challenge son…!Muchas Gracias!Queremos dar un enorme agradecimiento a todos los usuarios que participaron en nuestro primer Bitcoin Trading Challenge y ayudaron a que fuera todo un éxito, ya que hubo muchos más concursantes y participación de la que esperábamos.La mecánicaEl Bitcoin Trading Challenge tuvo una duración de un mes y se llevó a cabo entre el 15 de febrero y el 15 de marzo del 2016.
dogecoin exchange usdConsistió en acumular la mayor cantidad de volumen transaccional mediante la compra y venta de bitcoins en Bitso para escalar la tabla de posiciones.
legit bitcoin hardwareAsí se escogieron los 3 primeros lugares; y un premio especial mediante un sorteo entre todos los participantes que tuvieron por lo menos un bitcoin de volumen al final del concurso.
upstore bitcoin
Para el sorteo se extendieron boletos digitales por cada bitcoin de volúmen que se tuviera y se escogió al ganador al azar mediante una función ‘random’; 1 bitcoin = 1 boleto para participar.Los PremiosLos premios para lo ganadores del concurso son:Audífonos Beats by Dr. DreApple TVBitcoin Wallet TrezorPremio Especial: 1 bitcoinY los ganadores son:Queremos extender felicitaciones especiales para nuestros 4 ganadores:1.-2.-3.-Premio especial¡Felicidades a nuestros Ganadores!*Para proteger la privacidad de nuestros usuarios utilizamos el pseudónimo asignado para la participación en el concurso.Los ganadores han sido contactados y notificados y prometieron compartir con toda la comunidad una imagen disfrutando de su premio.Nuevamente muchas gracias a todos nuestros usuarios por participar y esperen nuevas y emocionantes promociones pronto.- Paco, Head of customer support.¿Tienes preguntas?
bitcoin piattaforma
no dudes en contactarnos.ShareHomeNewsFinance Brazil Will Only Use Registered Currency Come January 2017 Finance, NewsUn fanático de la banda de rock clásico Queen se ha convertido en el primer cliente en comprar boletos con bitcoin en Argentina a través de EntradaFan, según la compañía.Según difundió la compañía de capitales nacionales, se trata del primer boleto pagado con este tipo de valores en toda Latinoamérica.
comprar bitcoins tutorialLa alianza con la firma BitPagos hizo posible esta operación con bitcoin en Argentina.
litecoin using asicEste hecho ocurre en medio de un momento particularmente activo para bitcoin en Argentina, con la firma de servicios XAPO que recientemente firmó un acuerdo con la red social Taringa!
bitcoin core catching up
y cuando diversos medios de comunicación como The Wall Street Journal y The New York Times reseñan perfiles de crecimiento regional de la tecnología en éste país.Esta noticia confirma una vez más el creciente mercado de bitcoin en Argentina y además fortalece su posicionamiento entre las principales ciudades que adoptan bitcoin en todo el mundo.
ethereum key fileWhat Brazil’s Boleto Fraud Tells Us About Bitcoin and other Push Solutions When I explain to people how payment cards work, they are usually aghast.
bitcoin exchange ceo deathI point out that when you hand your card to a merchant and sign your name or enter your PIN, you’re authorising them to suck funds out of your account and the only thing that stops somebody draining all your money is trust.The picture below shows the standard “four-party” model for payment cards and I stress that the consumer is merely authorising payment; it’s the merchant and all the other actors who actually move the money.

The Payment Card “Four-Party” Model: Consumers authorise merchants to pull money out of their account.(Aside: I’ve never understood why this is called the four-party model.I count at least five parties on that picture…) Online, the problem is more stark: you type your card details, including your CVV2 “secret number on the back” into your browser and hope for the best: you have to trust the merchant, their IT supplier, the acquiring bank, their third-party processor, the card network and your own card issuer – and everybody who works for them and has access to their systems.If a bad guy gets hold of your card details at any point in this process, they could drain your account.The picture below shows the scope of all the entities with access to your critical card information: Your Primary Account Number – PAN – passes through the hands of pretty much everybody involved in processing the transaction.It seems mad: why would you spray such sensitive information all over the place willy-nilly?

Whoever thought it was a good idea to build the system this way?!Except… the system works.Fraud is surprisingly low given the design – and consumers get compensated if something goes wrong.And the design isn’t actually as mad as it seems: how else would you build a consumer payment network in a world where you can’t assume the consumer has a smart device with guaranteed network connectivity?Payment card networks also have the advantage of decades of experience and refinement.For example, the Payment Card Industry Data Security Standards (PCI-DSS) lay down rules and guidance on how to protect the sensitive card data.The EMV smartcard standards make it harder to clone cards.Issuers have sophisticated heuristics to block suspicious transactions.And forthcoming moves to standardise “tokenisation” (something I should blog about one day) will further mitigate the risk of card details getting into the wrong hands.So an underlying architecture that appears wholly unsuited to the web age has actually been patched up to be good enough (but not perfect – and it still has lots of problems) The Push Pay Revolution – a better way to do retail payments?

As I’ve written often, there is an entirely different way to design a retail payment system, one where the consumer doesn’t have to trust nearly as many people.I call these sort of payments push payments.Bitcoin follows this model, as does M-Pesa, iDEAL, ZAPP and the Boleto system in Brazil.The defining characteristic of push-payments is that the consumer is in the driving seat.With Push, it is the consumer who instructs a payment – from their bank or telco or Bitcoin wallet This is unlike pull-payments, where the consumer merely authorises the merchant to pull the funds from their account.The difference may seem subtle but it turns out to be hugely important.The picture to have in mind for push-payments is this one: Push payments have a very different threat model to pull payments.Now the consumer only has to trust their payment provider and their own device.In previous articles, I talked about the benefits of push payments in terms of innovation and the reduced need to trust quite so many people.

In this post, I look at one of the downsides: push payments can be compromised in hard-to-detect ways if they are not implemented really carefully.So what’s the problem with push payments?First, let’s remind ourselves about what we do have to trust and what we don’t have to trust in the pull world.In the pull world, the consumer has to trust everybody else – and, as I’ve discussed above, there are various safeguards in place to fix things when they inevitably go wrong.One might argue that the safeguards don’t always work and that they come at a cost.Both arguments are, of course, valid but let’s leave them to one side for now.In the push world, it’s different.The way it’s supposed to work is like this: To illustrate the point, here is a picture of me in Shoreditch trying to tell a Bitcoin ATM where to send some Bitcoins I’d bought.On my laptop screen is a QR code that represents my Bitcoin wallet address.Note how it’s me as the Bitcoin receiver who is telling the sender (the ATM) where to send the coins.

In the more common case, where I am paying Bitcoins, this means it is the merchant who has to show the QR code to me.I need to know where to send the money to.This is me using a QR code on my laptop to tell a Bitcoin ATM where to send my Bitcoins.(The Apple Bitcoin ban was still in force when we took this photo… so I had to use my laptop rather than my iPhone…) When you put it like this, push payments are obviously superior, right?The consumer is in control, they don’t have to trust all those people and there’s no danger of a rogue agent sucking all their money out of their account!The analysis above neglects one small, but rather important, fact: devices get hacked.In the pull model, the only devices that can get hacked are those inside the “circle of trust” – your plastic card is pretty impregnable.And as the utterly disastrous Target breach suggests, consumers were made whole when the disaster happened.It was the big firms who messed up who suffered the consequences.

Yes… I know this is counterintuitive… you must be asking yourselves: “is this guy seriously arguing that the Target disaster is an argument in favour of the current payment card model?!”the episode was clearly a catastrophe and it was really, really bad.But… it did eventually get sorted out and the roll-out of EMV, tokenisation and better enforcement of PCI-DSS should reduce the risks of something similar in the future.So I raise this merely as prelude to the push scenario.Now ask yourself what happens if a device gets hacked in the push scenario.The obvious question is: which device?Well… the only device in the circle-of-trust this time is the consumer’s smartphone.This is the device from which we’re instructing real-time payments, right?The one that could be riddled with malware?This might have been merely a theoretical risk….And then the Brazilian Boleto fraud happened.RSA have a great write-up of a country-scale real-life example of what can go wrong when push-payment systems get breached… and it’s really scary.

The Brazilian Boleto system is very cool.At core, it is a way for fund requestors (utility firms, etc) to send a payment request to consumers.The request is known as a Boleto and they can be physical or electronic.Think of it as a mainstream equivalent of a Bitcoin BIP70 Payment Request… The idea is this: the Boleto has details of the payment request and includes details of how much to pay and to where.This is in coded text format and a bar code… basically, something that a consumer can take and feed into their banking app: scan the code with your mobile banking app, approve and you’re done.Or you could take it to a bank branch.And if you’re online, you could copy and paste the code into your online banking website and achieve the same end.Except… the RSA paper shows all the ways it can and has gone wrong.First, there’s a simple problem of authentication.How do you know the Boleto really did come from who it says it’s from?The RSA paper documents examples of people receiving Boletos via email that look convincingly genuine but which have the fraudster’s payment account details in place of the firm from which they purport to come.

This is a real problem but it’s nothing new… it’s not really any different to fake websites that masquerade as real ones.We solved it in the pull world with SSL certificates and the like for websites.And the Bitcoin Payment Protocol includes the option to use the same PKI system, for precisely these reasons.However, the RSA paper also discusses another attack – and this one’s scarier.This second attack comes in the form of malware that runs in the consumer’s browser.When it sees a document that looks like a Boleto, it silently changes the details that the consumer sees on their screen: the payment details are changed from the genuine recipient to the attacker.So when the consumer copies and pastes the details into their banking app, it’s the attacker’s account they’re sending the money to.Variations on this theme are included in the paper but they all amount to the same thing: if the consumer’s device is compromised then it’s game over.And you don’t even need to compromise the whole device or get root-access… you just need to compromise the browser in this scenario.

There are various mitigation mechanisms one can implement (e.g.tying the payment instruction to a signed representation of the payment request and so forth) but the underlying problem remains: if you’re using the consumer device to instruct payments, you have an issue if that device is compromised.Now, this risk is perhaps over-blown: the risks identified here apply equally to standalone mobile banking apps and we happily run these on mobile devices today, albeit with the belief that their bank will bail them out if something goes wrong.(It’s no surprise that banks are big users of technology like IBM Trusteer).Similarly, Bitcoin users run their wallets on their devices, in the full knowledge that there is nobody who will bail them out if malware runs amok on the device.But I think the two-step dance of an end-to-end push payment request/instruction – where the device is responsible for turning the request into the instruction – is something new that needs deeper study.So I think the Boleto story tells us is that we need to think very hard about things like: It is possible that this is just a variation on the age-old theme that end-point security is hard – but when things like the Boleto fraud happen, we should use it as an opportunity to look at the other systems being built along similar lines and ask: are there any lessons we can learn and apply?