mine litecoin on iphone

All Things Online, Hardware, WindowsThe Complete LiteCoin Mining Guide For Windows 7Paying Cloud Mining Services Best Cloud Mining: Ranking by Daily ROI Top Paying Cloud Mining Services Top 10 Cloud Mining Services #StatusCloud Mining ContractsDaily ROI (%) * weekly averageDays to ROIComments HashFlare (ETH)0.22461 Hashnest (PACMiC 5)0.20500 ViaBTC (S9)0.16623 Genesis Min.(ETH)0.071478 HashFlare (Scrypt)0.061581 HashFlare (SHA-256)0.061796 BW (B-16)0.051956 Genesis Min.(Zcash)0.042777 HashFlare (Zcash)0.033850 HashFlare (X11)0.024525 All paying Cloud Minining Services #StatusCloud Mining ContractsDaily ROI (%) * weekly averageDays to ROIComments HashFlare (ETH)0.22461 Hashnest (PACMiC 5)0.20500 ViaBTC (S9)0.16623 Genesis Min.(Zcash)0.042777 HashFlare (Zcash)0.033850 HashFlare (X11)0.024525 Top Paying Cloud Mining Services Archive All201520162017 Bitcoin Cloud Mining Easy Bitcoin Mining Which content would you like to jump to?

u What is Cloud Mining?Types of Cloud Mining Hosted Mining vs.Buying Hasing Power Bitcoin Cloud Mining Pros Bitcoin Cloud Mining Cons Awesome Infographic!i Summary Useful Bitcoin Links and Information u What is Bitcoin Cloud Mining?The smart alternative of solo (hardware) mining Bitcoin Cloud Mining Overview Cloud Mining is a way to mine bitcoin (or different cryptocurrencies) without the need of owning a miner (or mining hardware).
bitcoin julian assangeSimply said, you buy yourself some shares of mining power – like a mining pool – and profit together with the pool.
bitcoin dragons denThis means that you only need a contract with someone who offers Cloud Mining Services and a bitcoin wallet (check out or bitcoin wallet guide!).
linux bitcoin miner gpu
Types of Cloud Mining There are two forms of cloud mining: Hosted Mining – You send your mining machine to a Firm, which provides electricity, cooling and configurations.It is also possible, that you lease yourself a mining machine.Buying Hashing Power – The most popular method of cloud mining – You buy an amount of hashing power (Hash Rate).Which means, that you don’t need to own a physical or virtual mining machine (computer).The pros of the one are the cons of the other and vice verse.Buying Hashing Power Now let us analyse both the Hosted Mining and the Buying Hashing Power types of bitcoin cloud mining.Starting with the pros of hosted mining: Less Scammy – if you decide to get an hosted bitcoin mining contract, than you need to check if the provider is a registered venture.If this is the case, you have high certainly, that you wont get scammed.Here is a list of hashing power cloud mining scam And now the cons of the hosted mining: Higher investment and monthly cost – you not only buy the mining machine, but need to maintanance costs depended on the energy use of the bitcoin miner.

Harder to Monitor – the success can be monitored only partly.Check out the our bitcoin cloud mining monitor to see the most profitable ones out there!The pros of the Hosted Mining are the cons of the Buying-Hashing-Power model and vice verse.Bitcoin Cloud Mining Pros Take a look on the benefits of bitcoin cloud mining: Higher Profits – because cloud mining providers optimize everything, it yields out higher returns.Tranquil and cooler home – no more permanent sound and heat.Less electricity – the electricity bills will get a lot lower.‘No’ equipment problems – no need to sell the bitcoin miners, when they stop being profitable.No need to configure the bitcoin hardware.Less risky – the possibility to get let down by the equipment is decreased by a lot.Bitcoin Cloud Mining Cons And now the counterpart list: Scam Risk – you can always have bad luck and find a cloud mining fraud.Cost of Mining Operations – you need to pay for the hardware management Less fun – at least for some it can be less fun to just virtually own something.

Lack of control and flexibility – harder to control where to mine or when to sell the bitcoin miner.Summary Bitcoin Cloud Mining is a way to mine bitcoin without owning mining hardware.Still, you need to decide which kind of cloud mining fits your needs best – Hosted or Bought- for which you should calculate how much you are willing to invest and how fast you want the Return of Investment (RoI) to be, be careful the higher the RoI the bigger the risk of getting scammed!Hint: Often writer use instead of Cloud Mining the wording Cloud Hashing and obviously instead of Bitcoin Cloud Mining – Bitcoin Cloud Hashing.Our Bitcoin Cloud Mining Infographic Well, after reading the hole text you deserve a REWARD! created a bitcoin infografic on How to make money with Bitcoin.This infographic should serve as a small guideline on how to optimize your bitcoin cloud mining earnings.We hope you like it.It’s our first bitcoin infografic… the next one will be even more awesome!Useful Bitcoin Links and Information After reading all this bitcoin cloud mining text here some things, which might interest you: Our Cloud Mining Monitor Our Bitcoin Faucet Guide Our Bitcoin HYIP Guide

Hackers have long used malware to enslave armies of unwitting PCs, but security researchers Rob Ragan and Oscar Salazar had a different thought: Why steal computing resources from innocent victims when there’s so much free processing power out there for the taking?At the Black Hat conference in Las Vegas next month Ragan and Salazar plan to reveal how they built a botnet using only free trials and freemium accounts on online application-hosting services—the kind coders use for development and testing to avoid having to buy their own servers and storage.The hacker duo used an automated process to generate unique email addresses and sign up for those free accounts en masse, assembling a cloud-based botnet of around a thousand computers.That online zombie horde was capable of launching coordinated cyberattacks, cracking passwords, or mining hundreds of dollars a day worth of cryptocurrency.And by assembling that botnet from cloud accounts rather than hijacked computers, Ragan and Salazar believe their creation may have even been legal.“We essentially built a supercomputer for free,” says Ragan, who along with Salazar works as a researcher for the security consultancy Bishop Fox.

“We’re definitely going to see more malicious activity coming out of these services.”Companies like Google, Heroku, Cloud Foundry, CloudBees, and many more offer developers the ability to host their applications on servers in faraway data centers, often reselling computing resources owned by companies like Amazon and Rackspace.Ragan and Salazar tested the account creation process for more than 150 of those services.Only a third of them required any credentials beyond an email address—additional information like a credit card, phone number, or filling out a captcha.Choosing among the easy two-thirds, they targeted about 15 services that let them sign up for a free account or a free trial.The researchers won’t name those vulnerable services, to avoid helping malicious hackers follow in their footsteps."A lot of these companies are startups trying to get as many users as quickly as possible," says Salazar."They’re not really thinking about defending against these kinds of attacks."Ragan
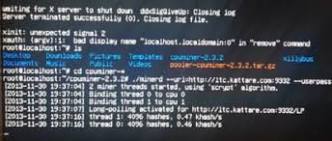
and Salazar created their automated rapid-fire signup and confirmation process with the email service Mandrill and their own program running on Google App Engine. let them create unlimited email addresses on different domains; to create realistic-looking addresses they used variations on actual addresses that they found dumped online after past data breaches.Then they used Python Fabric, a tool that lets developers manage multiple Python scripts, to control the hundreds of computers over which they had taken possession.One of their first experiments with their new cloud-based botnet was mining the cryptocurrency Litecoin.(That second-most-used cryptocoin is better suited to the cloud computers’ CPUs than Bitcoin, which is most easily mined with GPU chips.)They found that they could produce about 25 cents per account per day based on Litecoin’s exchange rates at the time.Putting their entire botnet behind that effort would have generated $1,750 a week.“And it’s all on someone else’s electricity bill,” says Ragan.Ragan and Salazar were wary of doing real damage by hogging the services’ electricity or processing, however, so they turned off their mining operation in a matter of hours.

For testing, however, they left a small number of mining programs running for two weeks.None were ever detected or shut down.Aside from Litecoin mining, the researchers say they could have used their cloudbots for more malicious ends—like distributed password-cracking, click fraud, or denial of service attacks that flood target websites with junk traffic.Because the cloud services offer far more networking bandwidth than the average home computer possesses, they say their botnet could have funneled about 20,000 PCs-worth of attack traffic at any given target.Ragan and Salazar weren’t able to actually measure the size of their attack, however, because none of their test targets were able to stay online long enough for an accurate reading.“We’re still looking for volunteers,” Ragan jokes.More disturbing yet, Ragan and Salazar say targets would find it especially tough to filter out an attack launched from reputable cloud services.“Imagine a distributed denial-of-service attack where the incoming IP addresses are all from Google and Amazon,” says Ragan.

“That becomes a challenge.You can’t blacklist that whole IP range.”Using a cloud-based botnet for that kind of attack, of course, would be illegal.But creating the botnet in the first place might not be, the two researchers argue.They admit they violated quite a few companies’ terms of service agreements, but it’s still a matter of legal debate whether such an action constitutes a crime.Breaking those fine print rules has contributed to some prosecutions under the Computer Fraud and Abuse Act, as in the case of the late Aaron Swartz.But at least one court has ruled that breaking terms of service alone doesn't constitute computer fraud.And the majority of terms of service violations go unpunished—a good thing given how few Internet users actually read them.Ragan and Salazar argue that regardless of legal protections, companies need to implement their own anti-automation techniques to prevent the kind of bot-based signups they demonstrated.At the time of their Black Hat talk, they plan to release both the software they used to create and control their cloudbots, as well as defense software they say can protect against their schemes.Other hackers, after all, haven’t been as polite as Ragan and Salazar in their cloud computing experiments.