bitcoin virus how to remove

A Facebook virus that mines Bitcoin has been discovered in Norway and is spreading rapidly across the globe.Experts call it a Norwegian phenomenon.The Facebook Virus is taking form as a Facebook direct message.If you have received a direct message on Facebook that looks like the image above then do not download or open it.Senior adviser Vidar Sandland from the Norwegian Center For Information Security (Norsis) warns Facebook users about the new virus.The virus was observed for the first time in Norway a week ago according to Norsis, and is spreading fast through the message system on Facebook.The computer gets infected as soon as you download the image and open the attachment.Your computer gets slower.The Facebook virus infects your computer and starts mining for Bitcoin and other cryptocurrencies.The mined cryptocurrencies are sent back to the perpetrators without the users know it.Your computer will make more noise and create more heat than it has done before because of the heavy calculations it’s doing by mining bitcoins.

In order to remove the mining virus you can do the following described by secarmour: You should also update your anti virus program, and if you do not have one, get one.The virus was first discovered by the Norwegian telecom giant Telenor.(Cryplocker, Cryptowall, Teslacrypt, etc...)reliable source ransom-ware tip: do not do thisProven Data Recovery [transmission begin] Happy Support Person : Greetings - I'm here to assist you if you have any questions.:) Cyndi, [formerly known as Happy Support Person: Hello Guest, my name is Cyndi [Last Name Omitted].I'll be with you just in a moment.dinbits [stealth: Yeah hello, I'm wonder about the Crypto-virus Data Recovery service, what is it that you can recover?Or is it just the removal and paying the ransom thing it asks for?Is this for personal or business use?dinbits [stealth: Both Okay.We would charge based on the variant of the virus you have and complexity involved in decrypting the data.

Our focus would be to decrypt the files and remove the virus.We have over a 90% success rate right now decrypting files from variance viruses.[transmission paused] 90% [transmission continued] dinbits [: Not sure what you mean by variant, this is asking me to register a wallet and purchase bitcoinz and send it to some long mix of letters and numbers then some other stuff, and that's about where I just stopped and decided to research.Variant meaning which version of the virus you have.CTB Locker, CryptoWall 2.0, 3.0, etc. [transmission paused] "Variant: .... [transmission continued] dinbits [: You have a picture of it on this page ... its the blue one CryptoWall 3.0 The image on Proven Data's Website Referred to : The current cost to decrypt and remove the virus is $1,800 to $5,000 for a single disk hard drive depending on the variant of your infection and the level of complexity involved in the recovery.We will first perform a free remote evaluation to determine the exact cost and provide you with a flat rate quote.

If you are interested in the free remote evaluation I can provide you with the next steps.justsend bitcoin "this is asking me to register a wallet and purchase bitcoinz and send it to some long mix of letters and numbers" Of course she knows this.
quickest bitcoin exchangealsoyou [transmission continued] dinbits [: Is that each?
amsterdam bitcoin centerIt's my home computer and my work laptop.
ethereum atm machineUnfortunately that would just be for the business computer ... [end of transmission] So what just happened here?$15,000.00.
bitcoin mining nvidia cardor to be fair: $900.00 @ (3 * 300 eaCryptowall creator/designer guyreal heist.$15,000.00 illegal wherecharging mepaying lying There are other ways to get your data back pointwrong.
small litecoin miner
with a success rate exceeding 90%, I might add Fulcrum Technologies, proven data years = 10^6(1.5) 2048cracking that's 4,294,967,296average*: *6.4 quadrillion years GREAT "We have over 6,000 geeks across the country in ...."
ethereum 1060before as many tuneups and virus removals as you want.
bitcoin new world order faucetiPhone best we'll do this for XX amounteither you pay the ransom and use the tool, or it's going to be difficult, expensive, and may not be possible at allabout $200plus the cost of the bitcoin no way are excessively illegal unethical If you find yourself in a jam, or if your running out of time, then don't worry!
harga bitcoin hari ini, and we'll be happy to walk you through the recovery for free.
bitcoin idag
Cryptolocker (also known as “Troj/Ransom-ACP”, “Trojan.Ransomcrypt.F”) is a Ransomware software that when it infects your computer, it encrypts all the files in it.The bad news with this virus is that, once it infects your computer, your critical files are encrypted with strong encryption and it is practically impossible to decrypt them.The Cryptolocker Ransomware demands that you make a payment of 300$ or 300€ in a specific period of time (e.g.72h or 100h), through a payment service (e.g.MoneyPak, Ukash, PaySafeCard, etc.)in order to unlock your files.otherwise -after that period- nobody can restore or decrypt them.The Cryptolocker is not a virus, but a malware software and it probably infects your computer when you open an email attachment from a legitimate sender that seems innocent or from your network shares or from an external USB drive that was plugged on your computer.Once Cryptolocker infects your computer, it starts to encrypt all personal files on your computer and then it sends the decryption key – known as “CryptoLocker ID” – to an online server.
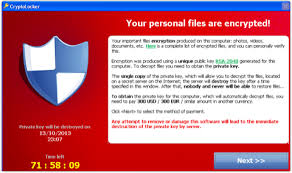
When Cryptolocker finishes encrypting your files, then a notification message comes on your screen demanding an immediate payment to unlock them.The message informs you that “Your personal files have been encrypted and you have 72 hours to pay us 300$”.From our research on several sites, we can inform our readers that in some cases, the files remain encrypted, despite the fact that the user makes the payment.So make this decision (to pay to unlock your files) at your own risk.The other choice is to remove CryptoLocker Ransomware infection from your computer, but in this case, you must realize that your files will remain encrypted, even if you disinfect your computer from this nasty malware.If you take this decision (to disinfect your computer) the only way to restore your files is from shadow copies by using Windows' “Restore previous versions” feature found at the latest operating systems.Update: (August 2014): FireEye & Fox-IT have released a new service that retrieves the private decryption key for users that were infected by the CryptoLocker ransomware.

The service is called 'DecryptCryptoLocker', (the service has discontinued) it is available globally and does not require users to register or provide contact information in order to use it.In order to use this service you have to visit this site: (the service has discontinued) and upload one encrypted CryptoLocker file from the infected computer (Notice: upload a file that doesn’t contain sensitive and/or private information).After you do that, you have to specify an email address in order to receive your private key and a link to download the decryption tool.Finally run the downloaded CryptoLocker decryption tool (locally on your computer) and enter your private key to decrypt your CryptoLocker encrypted files.More information about this service can be found here: FireEye and Fox-IT Announce New Service to Help CryptoLocker Victims.ONCE MORE: DO NOT CONTINUE TO REMOVE CRYPTOLOCKER VIRUS UNLESS: YOU HAVE A CLEAN BACKUP COPY OF YOUR FILES STORED IN A DIFFERENT PLACE (like an unplugged portable hard disk) YOU DON”T NEED THE ENCRYPTED FILES BECAUSE THEY ARE NOT SO IMPORTANT TO YOU.

YOU WANT TO GIVE IT A TRY TO RESTORE YOUR FILES USING SHADOW COPIES FEATURE (Step 5).So, if you have taken your final decision, then proceed first to remove Cryptolocker Ransomware infection from your computer and then try to restore your files by following the steps bellow: Windows 7, Vista & XP users: 1.Shut down your computer.Start up your computer (Power On) and, as your computer is booting up, press the "F8" key before the Windows logo appears.Using your keyboard arrows select the "Safe Mode with Networking" option and press "Enter".* Also works in Windows 7, Vista & XP.Press “Windows” + “R” keys to load the Run dialog box.Type “msconfig” and press Enter.Click the Boot tab and check “Safe Boot” & “Network”.Click “OK” and restart your computer.Note: In order to boot Windows in “Normal Mode” again, you have to uncheck the “Safe Boot” setting by using the same procedure.Download and save "RogueKiller" utility on your computer'* (e.g.your Desktop) Notice*: Download version x86 or X64 according to your operating system's version.

To find your operating system's version, "Right Click" on your computer icon, choose "Properties" and look at "System Type" section 2.Double Click to run RogueKiller.Let the prescan to complete and then press on "Scan" button to perform a full scan.When the full scan is completed, press the "Delete" button to remove all malicious items found.Close RogueKiller and proceed to the next Step.Download and install one of the most reliable FREE anti malware programs today to clean your computer from remaining malicious threats.If you want to stay constantly protected from malware threats, existing and future ones, we recommend that you install Malwarebytes Anti-Malware PRO: Malwarebytes™ Protection Removes Spyware, Adware & Malware.Start Your Free Download Now!Run "Malwarebytes Anti-Malware" and allow the program to update to it's latest version and malicious database if needed.When the "Malwarebytes Anti-Malware" main window appears on your screen, choose the "Perform quick scan" option and then press "Scan" button and let the program scan your system for threats.

When the scanning is completed, press “OK” to close the information message and then press the "Show results" button to view and remove the malicious threats found.At the "Show Results" window check – using your mouse's left button- all the infected objects and then choose the "Remove Selected" option and let the program remove the selected threats.When the removal of infected objects process is complete, "Restart your system to remove all active threats properly" 6.Continue to the next step.Notice: You must enable the hidden files view to perform this task.Navigate to the following paths and delete all Cryptolocker Hidden files: For Windows Vista or Windows 7: 2.Finally delete all files and folders under your TEMP folders: For Windows Vista or Windows 7: After you have disinfected your computer from Cryptolocker virus, then it is time to try to restore your files back to their state prior to the infection.For these methods, we use the Shadow Copy feature which is included in Windows XP and the latest operating systems (Windows 8, 7 & Vista) : Restore Cryptolocker encrypted files using Windows “Restore Previous versions” feature.

: Restore Cryptolocker encrypted files using Shadow Explorer.Method 1: Restore Cryptolocker encrypted files using Windows “Restore Previous versions” feature.How to restore CryptoLocker encrypted files using Windows “Restore Previous versions” feature: 1.Navigate to the folder or the file that you want to restore in a previous state and right-click on it.From the drop-down menu select “Restore Previous Versions”.* Notice* for Windows XP users: Select “Properties” and then the “Previous Versions” tab.Then choose a particular version of folder or file and the press the: How to restore CryptoLocker encrypted files using “Shadow Explorer” utility.ShadowExplorer, is a free replacement for the Previous Versions feature of Microsoft Windows Vista/ 7 / 8.You can restore lost or damaged files from Shadow Copies.Download ShadowExplorer utility from here.(You can either download the ShadowExplorer installer or the Portable version of the program).Run ShadowExplorer utility and then select the date that you want to restore the shadow copy of your folder/files.