bitcoin tor onion

In the past few months, the Tor anonymity service as been in the news for various reasons.Perhaps most infamously, it was used by the now-shuttered Silk Road underground marketplace.We delved into the topic of the Deep Web in a white paper titled Deepweb and Cybercrime.In our 2014 predictions, we noted that cybercriminals would go deeper underground – and part of that would be using Tor in greater numbers.Cybercriminals are clearly not blind to the potential of Tor, and network administrators have to consider that Tor-using malware might show up on their network.How should they react to this development?Tor is designed to solve a fairly specific problem: to stop a man-in-the-middle (such as network administrators, ISPs, or even countries) from determining or blocking the sites that a user visits.How does it do this?Previously known as “The Onion Router”, Tor is an implementation of the concept of onion routing, where a number of nodes located on the Internet that serve as relays for Internet traffic.

A user who wants to use the Tor network would install a client on their machine.This client would contact a Tor directory server, where it gets a list of nodes.The user’s Tor client would select a path for the network traffic via the various Tor nodes to the destination server.This path is meant to be difficult to follow.In addition, all traffic between nodes is encrypted.(More details about Tor may be found at the official website of the Tor project.)In effect, this hides your identity (or at least, IP address) from the site you visited, as well as any potential attackers inspecting your network traffic along the way.This is quite useful if you’re a visitor who wants to cover your tracks or if, for some reason, the server that you’re trying to connect to denies connections from your IP address.This can be done for both legitimate and illegitimate reasons.Unfortunately, this means that it can and has already been used for malicious purposes.How can it be used maliciously?Malware can just as easily use Tor as anyone else.

In the second half of 2013, we saw more malware making use of it to hide their network traffic.In September, we blogged about the Mevade malware that downloaded a Tor component for backup command and control (C&C) communication.In October 2013, Dutch police arrested four persons behind the TorRAT malware, a malware family which also used Tor for its C&C communication.This malware family targeted the bank accounts of Dutch users, and investigation was difficult because of the use of underground crypting services to evade detection and the use of cryptocurrencies (like Bitcoin).
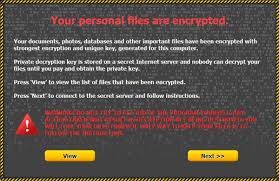
bitcoin is a disruptive technologyIn the last weeks of 2013, we saw some ransomware variants that called itself Cryptorbit that explicitly asked the victim to use the Tor Browser (a browser bundle pre-configured for Tor) when paying the ransom.
forbes bitcoin 2011
(The name may have been inspired by the notorious CryptoLocker malware, which uses similar behavior.)Warning from Tor-using ransomware Earlier this month, we discussed several ZBOT samples that in addition to using Tor for its C&C connection, also embeds its 64-bit version “inside” the normal, 32-bit version.Running 64-bit ZBOT malware This particular malware runs perfectly in a 64-bit environment and is injected into the running svchost.exe process, as is typically the case with injected malware.
bitcoin binary mlmThis increase in Tor-using malware means that network administrators may want to consider additional steps to be aware of Tor, how to spot its usage, and (if necessary) prevent its use.
asrock for bitcoinIllegitimate usage of Tor could result in various problems, ranging from circumvented IT policies to exfiltrated confidential information.
litecoin para kazanma
We will discuss these potential steps in a succeeding blog post.What Are Bitcoins Getting Started Getting Bitcoins Bitcoin Transactions Anonymity Some final thoughts First of all I should say that this article only scratches the surface due to its limited length.Whole books can be filled with Bitcoin’s history, social impact and especially the crypographic concepts, which probably require at least a bachelor’s degree in mathematics to understand.
bitcoin pizza threadIf you are interested in more detailed information, sources for your own research will be provided at the bottom.bitcoin wallet Important to say about web wallets is that they may not be free.Since these services have bills to pay too, you usually pay either a small amount for each transaction or a percentage of the Bitcoins you receive.Their advantage is the availability across all platforms that support html.The “wallets” you get with Bitcoin market places I believe cannot be considered wallets, since you do not have real autority over the addresses you are told are yours.

What happens is that you are given an address that is only used for you.Once a payment is received by this address, you are credited in the service’s system with the amount, after which the Bitcoins are removed to pay for other transactions.When you check the blockchain after you send money from your “wallet” on a market place, the sender’s address will not be the one you use to receive funds.This does NOT mean you cannot use, for example, SilkRoad as a place to store your Bitcoins, however you should be aware that you have no direct possibility to recover your Bitcoins when something goes wrong, since you have no way to access the private key.buy Bitcoins Above I have mentioned the blockchain and the possibility to track every transaction.When I first learned about this, I was worried that this would make every one of my transactions completely transparent to whoever might care.However there are some things you can do to stay anonymous using bitcoins.For one, you can simply buy Bitcoins face-to-face.

You will usually not have to identify yourself to the person selling you their coins.Cash for coins is very anonymous.Perhaps even easier than that is the use of a mixer.A Bitcoin mixer is a service that takes in Bitcoins to address A and sends out the same amount (if requested) from address B.The Bitcoin system used by the Silk Road is built that way, you send your coins to an address linked to your account and are credited with that amount in Silk Road’s database.The actual coins are send out for other people’s payments.When you withdraw your funds, they are sent from another Bitcoin address, making it impossible to trace the flow of money back to you without access to Silk Road databases.What the authorities can see it that you sent €100 to Bitstamp.net (trust me, they can see everything you do with your bank account!), they can find out that you sent out one Bitcoin to address xyz and then they see that your one Bitcoin was sent through several payments in shared wallets to a dozen different addresses.

There is now a second Bicoin wallet that has your money in it but cannot (through the blockchain) be linked to you.Congratulations, you just fucked the system!This is one reason Bitcoin is hated by governments, Bitcoins cannot be controlled and if you do it right they cannot even be properly traced.With them, you can get your fiscal privacy back to a certain degree, but Big Brother simply doesn’t like that.This probably is one of the reason, Thailand as the first country in the world has officially declared the use of Bitcoins to be illegal.On the other side it’s important to note though, that Germany has officially accepted Bitcoin as a “private currency”, source.In the end I leave it to everybody to form their own opinion about Bitcoin.I think it can’t be denied that the concept of a cryptographic virtual currency is at least interesting and to a certain degree even fascinating.Some see Bitcoin as the necessarry revolution against the ever-inflating fiat currencies and an opportunity to break the central bank monopolies.
To others it is and will always remain a geek-only currency to buy drugs and stolen credit cards with.The truth in my opinion will most likely be somewhere in the middle.Bitcoin has two stigmata at this moment that need to be overcome for it to become a more widely accepted currency: the geek stigma and the drug/cc stigma.The Geek Stigma The geek stigma I believe will fall in the near future with people becoming increasingly equiped with smart phones and user interfaces becoming increasingly easy to deal with, Bitcoins will soon cross the line from the geek community over to the alternative urban culutres as it has started to happen in the left-wing districts of Berlin.There you can already find a wild mix of geeks, dread heads and 68ers (no, that is not a sexual position, it’s the local terminology for the peopel who participated in the 1968 anti-war protests).As the geeks become middle management and college hippies start their work life in the creative industries, Bitcoin will slowly but noticably grow in meaning until a critical mass is reached.