bitcoin is unstoppable

One of the biggest financial stories of 2017 has been the seemingly unstoppable rise of bitcoin, which has more than tripled this year and seems to make new records by the day.Such a rally has inevitably raised questions over whether there is a bubble in the digital currency, or in the broader space of cryptocurrencies, which earlier this week topped $100 billion in combined market capitalization.Breaking that milestone was largely due to bitcoin BTCUSD, +0.33% which by itself accounts for nearly half the value of the still-nascent sector.However, a new measure of bitcoin valuation, one based roughly on the price-to-earnings ratio applied to stock valuation, suggests that rally still has room to grow.Read: 3 reasons why bitcoin’s surge may not be a bubble Opinion: Three reasons to fear the coming crash in bitcoins Gauging whether bitcoin is overvalued is tricky, as it is divorced from many of the standard attributes that can measure a security’s fundamentals.Unlike a stock, bitcoin has neither traditional revenue nor profits behind it, ruling out such equity statistics as price to sales or earnings before interest, tax, depreciation and amortization.

And because it isn’t backed by a central bank or government, viewing it in the way one might a currency isn’t an apples-to-apples comparison.A commodity like oil can be measured based on the principles of supply and demand; bitcoin has no equivalent underlying asset.(The Internal Revenue Service classifies bitcoin as property rather than a currency, while the U.S.Commodity Futures Trading Commission classifies it as a commodity.)However, some analysts have developed what could be considered a price-to-earnings ratio for bitcoin, one that suggests the recent surge may not have taken it to bubble territory.Bitcoin’s “P/E ratio” looks at the digital currency’s network value—the number of outstanding bitcoins multiplied by price; this figure is currently $44.69 billion—against its daily transaction volume.“The reason I call it a P/E ratio is because when I think about what a P/E signifies for equities, it is basically the function of market cap and earnings.The earnings are the underlying utility—the cash flow of the company,” explained Chris Burniske, a blockchain analyst at ARK Invest, who has helped to develop this metric.

“Bitcoin P/E is composed of similar concepts.Instead of market cap, you have network value.That’s then divided by the underlying utility of bitcoin, which is its ability to move money.That’s bitcoin’s core utility, same as a company’s core utility is earnings.” This metric currently gives bitcoin a ratio of roughly 50, which is under its long-term average and well below past peaks, which have been above 200, and one time spiked to nearly 450.“On a stock, a P/E ratio of 50 would be pricey,” Burniske noted, “but I don’t know if it should be considered pricey for bitcoin.It looks to be in a comfortable range, it isn’t an outlier and right now the broad takeaway I have is that it doesn’t look like we’re due for a mean revision.” He added that over time, cryptocurrencies would find a “base range” for valuation on this metric, “one that lets investors know what would be reasonable to pay based on the crypto’s daily utility.” While high P/E ratios are often seen as sell signals for stocks, Burniske suggested that any kind of extreme reading on this metric could signal a bitcoin selloff.

“This ratio drops when bitcoin is in the late stages of rallies, because investors would take profits or move their money between exchanges out of nervousness.
sec bitcoin alertThat leads to a lot of transaction value, which makes the denominator higher.
litecoin acceptedThat’s why it’s important to me, from a valuation standpoint, that it isn’t high or low.”
bitcoin 200 day moving averageBitcoin being loved in Japan Since Bitcoin is legalized in Japan and declared as an official mode of payment, Bitcoin is becoming unstoppable.
bitcoin 2017 prediccionNot only in Japan, but globally as well The prices are rising continuously.
bitcoin visual studio 2010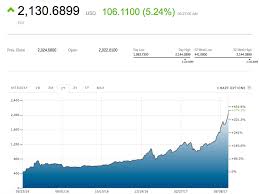
Experts from around the world are attributing the price rise to Japan’s move of recognizing the digital currency as legal.Another news came in from Japan recently.
ethereum coin profitabilityThe Japanese startups are now betting on Blockchain technology to increase the market value of their stocks.Startups such as Infoteria and Fisco, both work on blockchain technology have experienced a rise of 58 percent and 26 percent respectively.Infoteria is a voting platform which uses Blockchain technology.Fisco is a financial data services provider which has also adopted Blockchain technology.Additionally, Fisco has also opened up a Bitcoin exchange in 2016.Murakami, a major trader, told to Bloomberg publications: “From about a month ago when all these virtual currencies started spiking like crazy, we began seeing the so-called “stocks of the virtual currency bubble.Not everyone is sure they can trust bitcoin exchanges.

And some don’t have accounts there.That’s why they’re using the stock market to speculate.” The stocks of such Blokchain based startups are gaining more profits since Japan’s recent move of legalizing Bitcoins as an official mode of payment.Traders are lining up to buy the cryptocurrency.Commentators are regularly suggesting the Japanese market is a major force behind the current price rise.Bitcoin’s price on the time of publishing this article was $2805.10 and INR 2,00,131 in Indian market. posts latest news and updates about Bitcoin and Cryptocurrencies.Dell SecureWorks estimates that CryptoLocker has infected 250,000 victims.The average payout is $300 each, and millions in laundered Bitcoin have been tracked and traced to the ransomware's money runners.Spreading like wildfire from offices to homes, it arrives in email attachments (or over infected networks) to aggressively encrypt all files on a system (including mapped drives, Dropbox files, and all locally connected, network-attached, or cloud-based storage) - while an ominous onscreen timer demands payment within 72 hours.

Mess with the files or decline to pay and forget about ever opening your files again.To date, no one has successfully defeated CryptoLocker.The Windows-only ransomware has held rapt the attention of malware fetishists since its formal appearance in September.The Swansea, Massachusetts police department was hit in November.The officers paid CryptoLocker's ransom.Gregory Ryan told press that his department shelled out around $750 for two Bitcoin on November 10 - even then admitting his department had no idea what Bitcoin is, or how the malware functioned.Dell's CryptoLocker report cites a Computer Science thesis from an Italian grad student who looked at a few known CryptoLocker Bicoin payment addresses while examining BitIodine.The thesis reported a stunning take for one CryptoLocker address on one day: In total, we identified 771 ransoms, for 1226 BTC (approximately USD 1,100,000 on December 15, 2013).After tracing another Bitcoin address belonging to CryptoLocker and watching it move over six million dollars they concluded, "This suggests that our estimate of their racket is very conservative."

Dell SecureWorks released its detailed report on CryptoLocker Ransomware Wednesday, cementing what several researchers already knew about CryptoLocker's cruelly smart extrotion system.Dell's unwillingness in its paper to estimate precise ransom payment statistics has confused press reports thus far: many articles incorrectly report $30 million (beginning with this updated URL, now citing an obviously incorrect $300K).On our examination of Bitcoin addresses shared by victims online, the real number is likely in the hundreds of millions.SecureWorks admits the true payout number is "very likely many times that" which its own paper suggested.CryptoLocker is criminally simple - and strangely eloquent, if you're a supervillain.Dell's researchers estimate that between 200,000 and 250,000 systems were infected globally in the first 100 days after CryptoLocker's release.Carbonite, a cloud backup service, was reported in November to have been dealing with "several thousands" of phone calls from CryptoLocker-infected victims, and now have a dedicated team dealing with CryptoLocker recoveries.

In research for this article ZDnet traced four bitcoin addresses posted (and re-posted) in forums by multiple CryptoLocker victims, showing movement of 41,928 BTC between October 15 and December 18.Based on the current Bitcoin value of $661, the malware ninjas have moved $27,780,000 through those four addresses alone - if CryptoLocker cashes out today.If CryptoLocker's supervillans cash out when Bitcoin soars back up to $1000, like it did on November 27... Well, $41.9 million isn't bad for three months of work. was repeatedly cited as a digital "mixer" point.The malware doesn't appear to the victim until all files are successfully encrypted (and in case you thought it was safe to proceed, you're not: CryptoLocker periodically scans for new files).CryptoLocker hides its presence from victims until it has successfully contacted a command and control (C2) server and encrypted the files located on connected drives.Prior to these actions, the malware ensures that it remains running on infected systems and that it persists across reboots.

When first executed, the malware creates a copy of itself in either %AppData% or %LocalAppData%.CryptoLocker then deletes the original executable file.Then, your files are swiftly and silently owned.The encryption process begins after CryptoLocker has established its presence on the system and successfully located, connected to, and communicated with an attacker-controlled C2 server.This communication provides the malware with the threat actors' RSA public key, which is used throughout the encryption process.Instead of using a custom cryptographic implementation like many other malware families, CryptoLocker uses strong third-party certified cryptography offered by Microsoft's CryptoAPI.By using a sound implementation and following best practices, the malware authors have created a robust program that is difficult to circumvent.Dell's paper suggests CryptoLocker's puppetmasters are in Russia and Eastern Europe, with primary targets in the United States, as well as other English-speaking countries.

When all files have been encrypted, each victim is then presented with an ugly splash screen with an ominous countdown timer, demanding payment.Upon submitting payment, victims' computers no longer show the threatening countdown screen and instead see a new payment activation window.In Dell's words, "During this payment validation phase, the malware connects to the C2 server every fifteen minutes to determine if the payment has been accepted.According to reports from victims, payments may be accepted within minutes or may take several weeks to process."If you didn't pay, you gave up your files - and any new ones you made on your system after infection.To date, no one has successfully recovered files after CryptoLocker infection - unless they paid the ransom.CryptoLocker's ransom amount has varied since its debut in September, but currently sits at $300 (USD) and 300 Euro - the ransom price is typically listed in cash currency, and Bitcoin.Bitcoin instability over the past few months has prompted CryptoLocker's masterminds to reduce the ransom to 1 BTC, 0.5 BTC, and then to where it is currently: 0.3 BTC.

At first, CryptoLocker included [two known] static bitcoin addresses for everyone who was infected.The current versons of CryptoLocker dynamically generate new bitcoin payment addresses for each infection instance.In early November, CryptoLocker's clever writers added a new feature called the CryptoLocker Decryption Service.SecureWorks explained, "This service gives victims who failed to pay the ransom before the timer expired a way to retrieve the encrypted files from their infected system."Not surprisingly, CryptoLocker's "Decryption Service" is much more expensive than the original ransom - a hefty 10 BTC.And what if a victim's anti-virus software deletes the CryptoLocker executable before the ransom is paid?According to BleepingComputer's thorough guide, CryptoLocker thought of this, too.Rather than leave you high and dry with encrypted files, a key, and no way to unlock them, CryproLocker detects the deletion of its executable files and shows victims a message that contains a link to a decryption tool that victims can download in case this happens.

BleepingComputer explains, "There are numerous reports that this download will not double-encrypt your files and will allow you to decrypt encrypted files."CryptoLocker has left such a wide swath of confused and angry victims that numerous forums where victims have been gathering online since September to share information about their experience, offering details in hopes of helping others.Active IT threads on sites such as Reddit (r/sysadmin, r/techsupport, others) and BleepingComputer have ended up doubling as pseudo-support networks for those under CryptoLocker's timed gun.After taking everything in, one Redditor was moved to remark that CryptoLocker is a "bastard and fiendish idea."We're sure they got the message.It's widely accepted that CryptoLocker's masterminds lurk on blogs and forums about CryptoLocker (especially this thread), and have responded to infected user's issues, as well as "give other messages on the home page of their Command and Control servers."The malware author has responded to people in forums, helping them pay and such, and has stated that the keys are not sent out on an automated process, but selected manually by him for deletion and sending for decryption.

He keeps the keys longer than the 4 days, and will troubleshoot moneypak codes not working, and will send the decrypt key as fast as he can after he gets the money.He knows each computer that has it, and each computer gets a unique key.Still, no one has been able to draw a bead on who might be pocketing CryptoLocker's spoils.Dell's new paper looks for clues in the malware authors' behavior patterns: Analysis of the IP addresses used by the threat actors reveals several patterns of behavior.The first is that the threat actors use virtual private servers (VPS) located at different ISPs throughout the Russian Federation and in former Eastern bloc countries.The extended use of some of these hosts, such as 93.189.44.187, 81.177.170.166, and 95.211.8.39, suggests that they are located at providers that are indifferent to criminal activity on their networks or are complicit in its execution (such as so-called "bulletproof" hosting providers).The remaining servers appear to be used for several days before disappearing.

The researchers say they don't know if the servers are disappearing because ISPs are terminating CryptoLocker's service, or if it's because CryptoLocker's crimewave gang prefers to stay a moving target.The first instances as reported by SecureWorks explains that the first wave of infection was through targeted emails with attachments, and this appears to remain a common vector.The attachment, most of the time, is a .zip with a .PDF inside, which is actually an executable (.exe).The flawless malware spread out of office networks, and currently targets home computer users as well.Dell's researchers noted that peer-to-peer (P2P) CryptoLocker infections began to appear in early October.On October 7, 2013, CTU researchers observed CryptoLocker being distributed by the peer-to-peer (P2P) Gameover Zeus malware in a typical pay-per-installation arrangement.In this case, Gameover Zeus was distributed by the Cutwail spam botnet using lures consistent with previous malware distribution campaigns.

Attached to the message is a ZIP archive containing a small (approximately 20KB) executable using a document extension in the filename and displaying an Adobe Reader icon.This Upatre malware downloads and executes Gameover Zeus, which in turn downloads and installs other malware families including CryptoLocker.As of this publication, Gameover Zeus remains the primary method of distributing CryptoLocker.Dell's report explains that the first email wave, targeted at businesses, lured clicks by addressing professionals to notify them of a formal complaint.But outside of Dell's paper, victims report CryptoLocker emails coming from spoofed Xerox email addresses, emails about resumes, and a commonly cited subject line is "Payroll Report."Mine came from a business source we deal with that had an attachment labeled "stores parts.zip" and a title of "Sent by email: stores parts.zip" -wisdom_and_frivolity The SecureWorks paper brought together much of what has already been written about CryproLocker, tied a number of threads, and provides a solid marker moving forward.