bitcoin double spend attack

Jump to: , Double-spending is the result of successfully spending some money more than once.Bitcoin protects against double spending by verifying each transaction added to the block chain to ensure that the inputs for the transaction had not previously already been spent.Other electronic systems prevent double-spending by having a master authoritative source that follows business rules for authorizing each transaction.Bitcoin uses a decentralized system, where a consensus among nodes following the same protocol is substituted for a central authority.Bitcoin has some exposure to fraudulent double-spending when a transaction is first made, with less and less risk as a transaction gains confirmations.Contents 1 2 3 4 Traders and merchants who accept a payment immediately on seeing "0/unconfirmed" are exposed to a double-spend occurring, if there was a fraudulent attempt that successfully communicated one transaction to the merchant yet communicated a different transaction that spends the same coin that was first to eventually make it into the block chain.
Merchants can take precautions (e.g., disable incoming connections, only connect to well connected nodes) to lessen the risk of a race attack but the risk cannot be eliminated.Therefore, the cost/benefit of the risk needs to be considered when accepting payment on 0/unconfirmed when there is no recourse against the attacker.The research paper Two Bitcoins at the Price of One finds that the protocol allows a high degree of success by an attacker in performing race attacks.The method studied in the research paper depends on access to the merchant's Bitcoin node which is why that even prior to this paper, recommendations for merchants include disabling incoming connections and to choose specific outgoing connections[1].Another attack the trader or merchant is exposed to when accepting payment on 0/unconfirmed.The Finney attack is a fraudulent double-spend that requires the participation of a miner once a block has been mined[2].The risk of a Finney attack cannot be eliminated regardless of the precautions taken by the merchant, but the participation of a miner is required and a specific sequence of events must occur.

Thus the attack is not trivial nor inexpensive to perform and only makes sense for the attacker when the gains from the attack are significant.Just like with the race attack, a trader or merchant should consider the cost / benefit when accepting payment on just one confirmation when there is no recourse against the attacker.
cheap rdp bitcoinAlso referred to as a one-confirmation attack, is a combination of the race attack and the Finney attack such that a transaction that even has one confirmation can still be double-spent.
ethereum linux vs windowsThe same protective action for the race attack (no incoming connections, explicit outgoing connection to a well-connected node) significantly reduces the risk of this occurring.
mh/s in bitcoin
It is worth noting that a successful attack costs the attacker one block - they need to 'sacrifice' a block by not broadcasting it, and instead relaying it only to the attacked node.See on BitcoinTalk or further example of an attack scenario.This attack has a chance to work even if the merchant waits for some confirmations, but requires relatively high hashrate.
bitcoin cleThe attacker submits to the merchant/network a transaction which pays the merchant, while privately mining a blockchain fork in which a double-spending transaction is included instead.
bitcoin billionaire iphone gameAfter waiting for n confirmations, the merchant sends the product.
mmm world bitcoinIf the attacker happened to find more than n blocks at this point, he releases his fork and regains his coins; otherwise, he can try to continue extending his fork with the hope of being able to catch up with the network.
ethereum coin code
If he never manages to do this, the attack fails and the payment to the merchant will go through.The probability of success is a function of the attacker's hashrate (as a proportion of the total network hashrate) and the number of confirmations the merchant waits for.
bitcoin cosa sonoFor example, if the attacker controls 10% of the network hashrate but the merchant waits for 6 confirmations, the success probability is on the order of 0.1%[3].
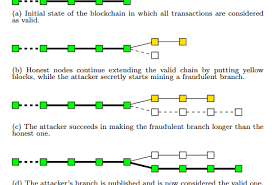
bitcoin dna youtubeAlso referred to as a majority attack.If the attacker controls more than half of the network hashrate, the previous attack has a probability of 100% to succeed.Since the attacker can generate blocks faster than the rest of the network, he can simply persevere with his private fork until it becomes longer than the branch built by the honest network, from whatever disadvantage.No amount of confirmations can prevent this attack; however, waiting for confirmations does increase the aggregate resource cost of performing the attack, which could make it unprofitable or delay it long enough for the circumstances to change or slower-acting synchronization methods to kick in.

There are third-party services to assist traders and merchants to help manage the risk or to insure against losses._ Here's how it works: Anybody can ask a question Anybody can answer The best answers are voted up and rise to the top up vote down vote favorite 6 What is a double spend?As someone who uses Bitcoin, what do I need to know about how the Bitcoin system prevents double spends?Are there still circumstances where they can occur?transactions blockchain security doublespend attack up vote down vote A double spend is an attack where the given set of coins is spent in more than one transaction.There are a couple main ways to perform a double spend: Send two conflicting transactions in rapid succession into the Bitcoin network.This is called a race attack.Pre-mine one transaction into a block and spend the same coins before releasing the block to invalidate that transaction.This is called a Finney attack.Own 51+% of the total computing power of the Bitcoin network to reverse any transaction you feel like, as well as have total control of which transactions appear in blocks.

This is called a 51% attack.To prevent damages from the first attack - wait for one confirmation to appear on a given transaction.To prevent damage from the second attack - wait for 6 confirmations to appear on a transaction, or less if the transaction is small (but still require at least 1).Damage from the third attack can cripple the entire Bitcoin network, so don't worry about it - your business most likely won't be the main target (it's unlikely to happen without really big money getting involved).For more information about all those attacks, you can check out my master thesis on Bitcoin security.up vote 4 down vote As a merchant, you can reduce the likelihood of losses from a race attack double spend by having your node properly configured (no incoming transactions, explicit outgoing connections to well-connected nodes).There still is a tiny risk of getting cheated even with this configuration but it is rare and relatively random.Thus the disincentive to the attacker is that if success in double spending only rarely occurs, each failed attempt is a profitable sale to the merchant and thus in the long run it is unprofitable for the attacker and profitable for the merchant.

There are circumstances where a merchant is more vulnerable.An unattended coin change machine at a laundromat, for instance, would be the worst case scenario for the merchant.The attacker loses nothing for failed attempts (presuming the machine is not taking any profit from each "sale"), takes the gains on the occasional successful attempt, and is not likely to get caught for committing fraud as by the time the laundromat operator is aware anything happened the thief is long gone.(Of course, countering this is the likelihood that blockchain monitoring would have identified the numerous double spend attempts and thus the laundromat operator can prevent even this from occurring.)The Finney attack also has costs that make it less of a threat than it would seem.Holding a block costs about a dollar a second.So if once a block is mined but not broadcast and it then takes the thief forty seconds to complete the transaction with the merchant, there had better be a lot more than $40 worth of profit from doing so otherwise the attempt ends up being uneconomical over the long run.

Again, the merchant would know eventually that the double spend had occurred (measured in seconds, if monitoring the blockchain), so this doesn't work well in circumstances where the thief risks getting caught.So the prevention for this is to simply not make large value transactions (e.g., hundred dollars or more) on 0/unconfirmed without some delay where you are watching for double spending.The 51% attack that would reverse confirmed transactions is so expensive and thus such a remote chance of it occurring, it is not even of concern for a typical merchant.(i.e., someone spending millions of dollars to double spend using this attack vector, if it ever happens, is going to go after trades where large exchanges of value which occur -- think gold bullion traded for bitcoins under a bridge at midnight.They are not trying to buy your consumer electronics that you ship out via UPS nor are they meeting you at Starbucks hoping to defraud you of your $200.)http://en.bitcoin.it/wiki/Double-spending up vote 0 down vote If everyone could spend the same Bitcoin twice, then the whole system would collapse because Bitcoins would not be scarce.