bitcoin core tor

It’s well known that bitcoin transactions are not anonymous.Every transaction and the full transaction history of any bitcoin address are permanently recorded in the tamper-proof public blockchain and open to analysis.A bitcoin addresses isn’t explicitly associated to its owner, but blockchain network analysis can often de-anonymize bitcoin users.Bitcoin Magazine recently reported that two companies, Chainalysis and Elliptic , sell sophisticated blockchain network analysis tools and services to trace bitcoin transactions back to their participants, and de-anonymize users.Such services often anger libertarian early adopters, but the direction of the evolutionary trend in the Bitcoin space is clear – governments and financial institutions are gradually warming up to blockchain technology as a means to achieve faster, cheaper and better recorded transactions, but consider privacy and anonymity as bugs that need to be fixed.Recommended privacy practices, from simple measures such as using fresh Bitcoin addresses for new transactions to strong privacy measures such as dark wallets and mixing services, reduce the risk of being de-anonymized, but there are documented attack strategies that often permit identifying bitcoin users by IP.

Using the Tor network provides additional privacy protection by masking the user’s IP, but ways to work around Tor privacy have been found.Now two researchers from the ATR Defense Science & Technology Lab at Shenzhen University, in China, have published a white paper titled “Transaction Remote Release (TRR): A New Anonymization Technology for Bitcoin .” The researchers propose a new anonymization technology called Transaction Remote Release (TRR).Inspired by Tor, TRR is able to render several typical attack strategies ineffective.“Furthermore, the performance of encryption and decryption of TRR is good and the growth rate of the cipher is very limited,” say the researchers.“Hence, TRR is suited for practical applications.” “In the Bitcoin protocol, the only way that the attackers can connect the Bitcoin address with an IP address is in the process of releasing and spreading a new transaction,” note the researchers.Therefore, they propose to encrypt the new transaction and obfuscate the source IP of the sender.
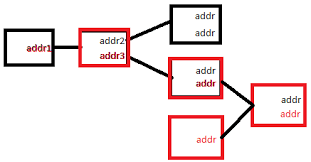
TRR is inspired by the idea of encryption and decryption layer by layer as used in Tor.A client encrypts a new transaction, layer by layer, using the public key from different TRR nodes.Then it establishes an independent connection to other TRR nodes, one by one, without using the spreading mechanism of the Bitcoin network.When a TRR node receives data, it will decrypt it using its private key.Then it transmits the remaining data to the next node.
dogecoin rate chartWhen the last TRR node is reached, it will release the transaction to the Bitcoin network.
bitcoin hatersEvery node knows its previous node and next node.
bitcoin bowl scoreOnly the client and the last node know the content of the transaction but the last node does not know the IP address of the client.The researchers analyze several possible de-anonymization attack strategies, including Bitcoin protocol sniffers, the Sybil attack, Sybil attack plus entry nodes, fake Bitcoin nodes and fake TRR nodes attack, and conclude that TRR can help clients gain strong anonymity.

"In addition, the experiments show that the performance of the TRR multi-layered encryption and decryption algorithm is satisfactory in practice and the growth rate of cipher text is very limited,” note the researchers in the conclusion.The researchers acknowledge that the current TRR proposal is vulnerable to DoS attacks based on fake TRR requests, and state that further research to eliminate this weakness is ongoing.But another weakness is that implementing TRR would require changes to the Bitcoin protocol.That is a serious weakness, because it seems evident that, in the privacy-as-bug climate that is developing around Bitcoin, there is just no way modifications to Bitcoin Core explicitly aimed at anonymity could ever be accepted.Therefore, it might make more sense to consider implementing TRR in a privacy-enhanced sidechain.The modifications to Bitcoin Core required for implementing sidechains are justified by general considerations much more acceptable from a mainstream perspective.

Sidechain Elements , the first experimental code base for sidechains released by Blockstream, includes confidential transactions, and a sidechain implementation of TRR could be a workable way to sneak privacy in.The popular website Daily Dot covered the TRR white paper and noted that TRR first emerged in 2014 during the development of DarkNetCoin, a niche cryptocurrency focused on anonymity.Unfortunately the conclusion of the Daily Dot article, “Bitcoin did not respond to a request for comment about TRR,” reveals that the mainstream press still has basic things to learn about Bitcoin.In this post I’m going to describe my ongoing experiment of porting Bitcoin Core to CloudABI.I think the capability-based approach of CloudABI is a conceptually great way of going about the problem of containing applications, and it might be a harbinger of things to come in computer security.Bitcoin Core is a good example of an existing, moderately complex, security critical C++ application to port over.

CloudABI is a new open source project for sandboxing applications.The goal is to isolate an application so that it can only access what it needs, and only by way of the provided access methods.This hardens against both privilege escalations and privacy leaks.What sets it apart from other sandboxing methods is that: The system call ABI is as minimal as possible to reduce attack surface.It is defined in an OS-agnostic way.CloudABI has its own C library that only defines what is offered by this ABI.Security is based on capabilities, represented as file descriptors.There are no global namespace, everything that the application needs must be passed in explicitly.This is defined using a standardized configuration file.These properties allows cloudabi executables to run on different operating systems unmodified (FreeBSD, NetBSD, Linux at this time).A restricted ABI and special libc means that it is easy to find out whether something will work: compile it.

This is different from low-level sandboxing such as seccomp-bpf, where all system calls potentially used need to be carefully enumerated.This is difficult - especially when a project makes use of libraries not under the developer’s control, as any moderately complex program does.There is a runtime crash if a process exceeds its permissions, risking fragility.CloudABI thus allows porting applications to a strictly sandboxed environment in a robust way.The following is an overview of the challenges encountered while porting Bitcoin Core to this new ABI.CloudABI applications can make use of files, but do not have access to the global file system space.Access to directories must be explicitly granted by passing in a directory file descriptor.openat() and similar functions can then be used to open files relative to those directories only.Bitcoin Core virtually only accesses files within its data directory.So for most of the functionality, passing in a handle to the data directory is enough.
It could be stored in a global and used where necessary.All filenames are then relative to that.In the future, different file handles could be passed in for the different directories, e.g.to place the block index somewhere else as that wallet.But this functionality is not available in the upstream implementation either (except by a symlink hack) so the infrastructure still has to be writtenanyhow.Bitcoin Core uses boost::filesystem for all file and path manipulation.It looks like boost::filesystem doesn’t work with cloudabi.It is possible to make use of path, however this has no special intelligence to handle fd-relative paths.None of the file or directory operations work.The good thing about this is that (nearly) all uses of paths are already abstracted, so what I thought is the best way forward is to make a boost::filesystem::path subset replacement that works with paths relative to fds, and implements the file operations for this platform.

For this reason I created the fs.h filesystem abstraction.A file descriptor for log output should be passed in, to aid in debugging.CloudABI applications cannot listen on a port, nor directly connect out to the network, which poses some challenges.Binding sockets for RPC and P2P must be passed in through the argdata API.You could say that for a P2P client it is fairly important to be able to make outgoing connections.Outgoing network connections are not possible without an external helper.A simple workaround for this would be to use of a SOCKS proxy (such as Tor) which acts as guard.File descriptors of connections to this proxy would be passed in by an external utility (although I’m not sure how this is done yet).Alternatively the proxy could be made connect in to the process to “reverse proxy” when asked over a control socket.No capability to make outgoing connections also means no DNS lookups.This is all too well; DNS leaks are a common privacy leak.

DNS lookup in Bitcoin Core is mostly used for requesting node addresses from the DNS seeds, which are used for outgoing connections.So any solution that enabled external connections could potentially allow doing this too (e.g.Tor has a SOCKS5 extension for DNS lookup).Argument passing is another thing that is different for CloudABI.Instead of an array of parameters like in most operating systems, a nested structure (to be precise, a binary representation of YAML) is passed in.There is nothing forbidding passing all configuration arguments in one array within the structure and simply passing that to ParseParameters as if it came in in argc and argv.However, we can do better.Instead I’ve opted to add argument processing code to take a map of option name to option value(s).An example configuration: !: : : : : : : : : 1 : " : " : 0 : [",","] : 0 : This gives the bitcoind process a handle to its data directory, to stdout for logging output, and passes in two readily listening network sockets for RPC and P2P.

The standard bitcoind arguments are passed in args.The following dependencies have already been ported by the CloudABI project: The following might need to be ported (but see under “Missing Features”): These would be pointless in CloudABI: These features are currently missing in the CloudABI port, either until implemented or cannot be supported as they inherently mismatch the goals of CloudABI.Wallet support: Need porting over BerkeleyDB, or maybe changing the wallet database format to something that doesn’t rely on this library.bitcoin.conf parsing is currently disabled due to use of boost::fstream, which isn’t part of my wrapper yet.It is however possible to pass all bitcoin.conf settings using the input YAML file, in the args map (as shown above), so it is of lesser priority.mlock/lock: These calls don’t exist on CloudABI.Would be nice to have an alternative way to pass in a chunk of pre-mlocked memory, but I’m not sure how.

As Bitcoin Core only uses memory locking to keep private key data out of swap, this is not an issue until the wallet is supported.External script notifications: Notifications that call out to external scripts using system(), such as used for -blocknotify and -walletnotify are disabled.As it can only inherit bitcoind’s restricted capabilities, there is nothing useful that such a script could do.Network-based notifications will have to be used (ZeroMQ is available, another option is long-polling over RPC which is in the works).Torcontrol: To support this, a handle to the Tor control socket could be passed in.This can be left for later as there are some additional challenges here, and for this use it’s more straightforward to configure Tor and bitcoin statically.The current version of this work can be found in my 2017_03_cabi_fs branch.Edit.1: Remove mention that ZeroMQ is not ported.It has been ported now.Edit.2: Soften requirement to port BerkeleyDB.