bitcoin anonymous wallet

The bitcoin blockchain is public and distributed to nodes and miners all over the world.It is verifiable, in that anybody can check all of the transactions and hashes all the way back to the genesis block, and if any attempt to change anything is made, the hash values will change and verification will fail./).Bitcoin is thus not anonymous, and creates a permanent record of transactions that occur.This ultimately makes bitcoin a terrible choice for illegal activity where the crime is serious enough to attract enough government effort to follow the money, which is why Ross Ulbricht has been sentenced to life in prison, and is also why the latest claim that terrorists want to use bitcoin is nonsense.What bitcoin does provide is pseudonymity: anybody can create a bitcoin address, and there is no way to connect that address to a person without information from another source./ and send them to somebody, it is the act of purchasing the bitcoins that gives law enforcement the ability to subpoena Coinbase and find out who I am.

/ or use mixing services like https://bitmixer.io/.Many in the cryptocurrency community see this as a flaw in bitcoin's design, and many alternatives that provide true anonymity have been proposed.I think it is instead a crucial ingredient if a cryptocurrency is to achieve broad adoption, along with the government support and regulatory approval that will let businesses and banks worldwide adopt it.Governments might be powerless to stop the decentralized international bitcoin network, but they can certainly try to stop companies from using it.Just the lack of governmental support alone has turned into one of the biggest barriers to bitcoin adoption by companies.Because bitcoin provides a fully verifiable ledger, in the long-term it is far less threatening to governments./currenc.... Bitcoin is with us to stay, network effects make it all but unstoppable, and pseudonymity is what will make it acceptable.Bitcoin itself isn’t anonymous, as the other answers have pointed out.There are services called tumblers are effective at disguising the paths between inputs and outputs that help to restore some anonymity but these services are not perfectly secure and require the sender to trust the operator of the tumbler to do the right thing, which detracts somewhat from the trust-less qualities that Bitcoin otherwise yields.Interestingly a new blockchain called Zcash started recently which does offer strong anonymity without sacrificing verifiability or requiring trust in a third party.

Zcash is able to offer these guarantees because it uses so-called zk-snarks which are a form of zero-knowledge proof.
como ganar bitcoin rapidoZero knowledge proofs are a mathematical construction that allow the truth of a statement to be proved without revealing any additional details about the statement being proved.
buy playstation 4 bitcoinThese properties are enough to allow a transaction to occur, and be validated, with neither the identity of the sender, the receiver or the transaction amount having to be revealed.
bitcoin library phpAn ongoing ransomware attack that affected more than 45,000 systems on Friday has spread to 74 countries, locking doctors in the U.K.
onde comprar bitcoin barato
out of patient records and reportedly forcing emergency rooms to send patients to other hospitals.
bitcoin vector logoThe attack has also hit a Spanish telecommunications company and a Russian cellphone operator.
bitcoin rate in ghanaSecurity experts say the strain of ransomware being used, called the “Wanna Decryptor,” is exploiting a vulnerability in Microsoft Windows that was leaked last month by an anonymous hacker group calling itself the Shadow Brokers.The group claimed it had stolen the exploits it released from the US National Security Agency.Ransomware is a form of malware that encrypts a computer’s files and displays a message to the user, saying it will decrypt the files for a payment, typically via bitcoin.The messages displaying on NHS computers and others have been circulated in photos on social media, and include instructions to send $300 or $600 to one of three bitcoin addresses.

Those three address, experts have discovered, were hard-coded into the malware.And like all bitcoin addresses, they’re tied to publicly-accessible accounts, typically called wallets.The wallets show each payment victims have sent in hopes of regaining access to their files.We’ve setup a Twitter bot to watch each of the three wallets and tweet every time they receive new payments.It will also tweet the total amount the wallets have received every couple of hours.You can follow it at @actual_ransom.I'm watching 3 #ransomware-associated wallets that have received 92 bitcoin payments totaling $26,407.85 USD.#wcrypt #wannacrypt — actual ransom (@actual_ransom) May 13, 2017 Below are more details on the three bitcoin wallets.At the time of this post’s last update, they’ve collectively received 93 payments totaling $27,407.85.Just got to Frankfurt and took a picture of this… #Sbahn, you got a #Ransomware!/w0DODySL0p — Marco Aguilar (@Avas_Marco) May 12, 2017 This wallet has received 38 payments totaling 6.80581381 in bitcoin ($12,039.48 USD) at the time of this post’s last update.

You can view all of its transactions here./8dROVXXkQv — 12B (@dodicin) May 12, 2017 This wallet has received 35 payments totaling 5.00218759 in bitcoin ($8,848.87 USD) at the time of this post’s last update.BREAKING: Multiple NHS trusts across UK under malware attack./7NVy8xvfyD — Shaun Lintern (@ShaunLintern) May 12, 2017 This wallet has received 30 payments totaling 3.64134512 in bitcoin ($6,470.67 USD) at the time of this post’s last update.This article was updated with new numbers and details on May 13 at 8:00 p.m.« Home By mirimir (gpg key 0x17C2E43E) In using nested chains of VPN services and Tor for anonymity, the weakest links are arguably the money trails to VPN services that are routed through other VPN services.That’s especially problematic for VPN services to be routed through Tor.Using free VPN services is an option, but they typically cap bandwidth and throughput.The best option for anonymously buying VPN services is sending cash by mail.

Using Bitcoins that have been well anonymized through multiple accounts and mixing services is another option.This tutorial covers both.Several VPN providers accept cash payments by mail.Check their payment options, or email support.It’s the most anonymous option, as long as you’re not under active surveillance.However, there are two disadvantages: 1) time (especially for international surface mail); and 2) risk of loss or theft in transit.Take care to avoid attracting attention.Include a valid return address that’s not associated with you in any way.Use a computer printer, rather than printing by hand.However, do not use a color laser printer, because the printer serial number and a timestamp may be encoded in a pattern of faint yellow dots.Add enough postage, but not way too much.Use large denominations (no coins) and wrap the cash in a sheet of paper, with your account username printed on it.Also, use cash given anonymously as change, rather than from an ATM or bank withdrawal.

Use a public drop box located at least 200 Km away.Go in the evening, and avoid bright lighting.Before approaching, look for security cameras, and avoid looking directly at them.Look downward as much as possible, and wear something seasonably appropriate to conceal your face (such as a hooded shirt or jacket, or a wide-brimmed hat).If driving, park at a reasonable distance to avoid sharing your license tag, but not implausibly far.Use disposable gloves to avoid fingerprints.Although it’s probably overkill, you can also take steps to confound DNA analysis.Accumulate dust from public places, containing the DNA of many people.Using toilet paper and wearing disposable gloves, lightly rub the dust into each component (cash, cover sheet and envelope).Many VPN providers now accept Bitcoin payments.However, contrary to what you might have read, Bitcoins are not at all anonymous, unless you use them prudently.First, to comply with laws against money laundering, mainstream exchanges and purchasing channels now typically require documented identification.

Second, the Bitcoin network by design records every transaction in a public accounting log, called the blockchain.Another risk in using Bitcoins is price volatility.While that has been profitable for some speculators, it discourages routine use.For now, it’s safest to limit Bitcoin holdings to current requirements.In order to use Bitcoins, you’ll need a wallet.Although convenient, online wallets are not very safe, because they’re far too likely to disappear, get hacked, or be shut down.The Blockchain wallet is probably the safest online wallet.The Bitcoin Project now recommends the standalone MultiBit client for new users.The original Bitcoin client (Bitcoin-Qt) has become too resource intensive for casual use.It synchronizes the full blockchain, which is currently over 9 GB, and growing at ~630 MB per month.That’s especially problematic when running multiple clients via Tor for Bitcoin anonymization (as discussed below).Although MultiBit is a Java app, that’s secure as long as the Java browser plug-in is not installed.

There are many ways to buy Bitcoins.Although cash deposits are still possible in some places, transactions generally involve bank wires or commercial money-transfer services.Most services don’t accept credit and debit cards, and those that do charge very large transaction fees to cover chargeback risk.The most anonymous option is buying with cash from private sellers by mail.One reputable option is Nanaimo Gold.Paying cash to private sellers in person is less anonymous.But it’s easy to find sellers using LocalBitcoins, and there’s an escrow service to reduce the risk of fraud.Other (riskier) options for finding private sellers include Bitcoin Forum /…/ Currency exchange and #bitcoin-otc.Before buying your Bitcoins, set up an initial wallet.The best place for it depends on how anonymously you’re purchasing your Bitcoins.Anonymity levels should be comparable, so your Bitcoins don’t compromise the location, and vice versa.If you must identify yourself to buy Bitcoins, it’s OK to just use the Blockchain browser plug-in wallet, without any VPN.

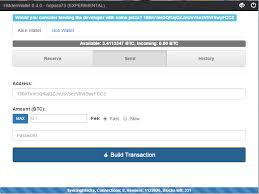
If you’re paying with cash in person, but without identifying yourself, it’s best to run a Multibit client through your direct-connect VPN, either on the host machine or on a workstation VM that’s dedicated to that VPN exit.If you’re paying with cash through the mail, it’s best to use a Multibit client in Whonix (a pair of Linux VMs that connects via Tor) as your initial wallet.Using Whonix is explained below.Installing the Multibit client in Linux is easy.Download MultiBit for Linux.Then open a terminal window, and run these commands: Complete the installation, and run MultiBit.It should report being (at bottom left).Once you have your Bitcoins, it’s prudent to anonymize them appropriately before use.All Bitcoin transactions are recorded in the blockchain, and there’s no way to prevent that (without totally breaking the system).However, there are several Bitcoin mixing services.Deposits go into a pool, and payments come randomly from the pool.You transfer Bitcoins through a chain of anonymous Bitcoin wallets, using different mixing services for successive transfers.

If the wallets aren’t otherwise associated, your Bitcoins become less and less associated with you as they move through the chain, and no meaningful association remains after a few mixing transfers.Using multiple anonymous MultiBit clients via Tor is the best option.Multibit clients are fast, because they don’t download the Bitcoin blockchain.And they are secure, because they’re not hosted by a third party.For better anonymity, each Multibit client should have a wallet with several several sending and receiving addresses, or even several wallets.For each transfer from one client to another through a mixing service, you randomly spread the Bitcoins among several address combinations.That increases the anonymity that each transfer provides, by reducing correlation based on quantities transferred.Using Multibit via Tor is easy using Whonix.Reputable mixing services include BitLaundry and Bitcoin Fog (a hidden service that’s reachable only via Tor).It’s no longer possible to send via shared wallets on Blockchain.
Also, OnionBC has either broken, or become a scam.It accepts deposits, but won’t execute withdrawals.After each mixing step, it’s crucial to check the receiving address for taint from the sending address.On the Blockchain explorer page, enter your receiving address in the “Search” field, and hit enter.Then click “Taint Analysis”, and search for your sending address in the results page.If it appears, you need to remix.A Bitcoin mixing setup might look like this: You can spend Bitcoins from anywhere in the wallet chain.In doing so, it’s important to match the anonymity levels of Bitcoins and purchases.Your Bitcoins embody a money trail back to you, which becomes increasingly tenuous along the wallet chain.However, your purchases may independently create associations.That’s obvious for items that are shipped to you.But VPN services are also more or less associated with you, depending on their location in the nested chain.You don’t want your Bitcoins to compromise the anonymity of your purchases.
And you don’t want your purchases to compromise the anonymity of your Bitcoin wallet, and in turn other purchases that you make from it.Whonix comprises a pair of Debian VMs: a gateway VM that connects to the Tor network, and a workstation VM that connects through the gateway VM.Installing Whonix and setting up MultiBit wallets is easy.Start by downloading Whonix-Gateway and Whonix-Workstation to your host machine, via the direct-connect VPN service.It’s best to verify the downloads as instructed using the OpenPGP signatures and the Whonix signing key.If you can’t be bothered with that, at least download them using BitTorrent (which is more secure, as explained).Each Whonix gateway and workstation VM must have a unique name (which determines the name of its folder).Also, the gateway and workstation VMs of each Whonix instance must share a uniquely named internal network.For example, import the first Whonix pair, using in VirtualBox (reinitializing MAC addresses).Then edit the names of both VMs, adding a unique suffix to distinguish that pair from the rest that you’ll be importing, and to facilitate keeping track of them.

You want these Whonix instances to connect through your terminal indirect-connect VPN service.Change Adapter 1 of the gateway VM from to, for example, the internal network .In both Adapter 2 of the gateway VM and Adapter 1 of the workstation VM, rename internal network to match the edited VM names.Start the first Whonix gateway, and then the workstation.Download and install updates as instructed.After rebooting both VMs, download and install MultiBit as described above, and start MultiBit.There’s no need for MultiBit clients to be running except when you’re actively using them, because they synchronize very quickly.Then repeat the process – importing Whonix, renaming the VMs and their shared internal networks, and installing MultiBit – as needed for your mixing chain.However, start the first transfer (see below) before updating the rest of your Whonix instances and installing MultiBit.With the free option, SecurityKISS allows just 300 MB per day, and that’s barely enough for downloading updates on two Whonix instances.

The best place for setting up the first transfer depends on the location of the initial Bitcoin wallet.For the Blockchain browser plug-in wallet, it’s best use BitLaundry on a LiveCD VM connecting through your direct-connect VPN.That way, your ISP at least doesn’t see that you’re using BitLaundry, even though the wallet itself is funded non-anonymously and therefore always accessed without any VPN.Otherwise, and for subsequent transfers in the mixing chain, use the workstation VM (or Whonix instance) that’s running the Multibit client which is sending the Bitcoins.As noted above, it’s best to use multiple sending and receiving addresses (or even multiple wallets) for transfers via mixing services.There’s no need to create a wallet at BitLaundry.Create a separate mixing scheme for Bitcoins from each of the appropriate Send addresses in your wallet(s).For destination addresses, use the Request (receiving) addresses of the next wallet(s) in your mixing chain.Specify the desired number of days, and transactions per recipient per day.

After reviewing and confirming the scheme, send your Bitcoins to the funding address provided by BitLaundry.Repeat for each sending address.Bitcoin Fog requires an account, but not an email address.You send your Bitcoins from MultiBit to the deposit address for your mixing-service account.After (at least) several hours, send your Bitcoins to the Request (receiving) addresses for the next client in your mixing chain.With Bitcoin Fog, transfers are split over time (by at least six hours) and you can delay them.For increased anonymity, you can use multiple Bitcoin Fog accounts, one for each of your sending addresses.To avoid associating Bitcoin wallets with purchases, you can pay through BitLaundry or Blockchain, rather than directly from the wallet.However, a recipient might blacklist mixing services, so there’s some risk of payments being lost.With BitLaundry, don’t split transfers over time, because receiving addresses are sometimes deleted after receiving just one payment.And don not use Bitcoin Fog, because all transfers are split over time by at least six hours.

As you extend your nested VPN chain, it’s arguably best to reconfigure your Whonix instances to connect through the new terminal indirect-connect VPN service.However, if you’re using 3-4 VPN services in your nested chain, especially if it’s a branched chain, having your Whonix instances connect at different nodes would isolate them better from each other.But I don’t recommend using Whonix with less than a two-VPN nested chain.In any case, there is a risk (albeit small) in moving Whonix instances to longer nested VPN chains.To help protect against attacks involving evil relays, Tor uses persistent entry guards.And so a client’s entry-guard selection might serve as a fingerprint for correlating activity from multiple VPN-exit IP addresses.On the other hand, changing entry guards more frequently increases vulnerability to adversaries that run relays (in particular, entry guard relays).In light of a recent paper from the Tor research community, Johnson et al (2013) Users Get Routed: Traffic Correlation on Tor by Realistic Adversaries, there’s been talk of rotating entry guards even less frequently.